A Wizer Guide For Effective Phishing Simulation Templates
As the year draws to a close, it’s time to look back on the phishing simulation templates we’ve covered throughout our monthly series. We want to help those running phishing programs to know the ‘why’ of every template they select, to make sure their campaigns are much more than just seeing if employees click or not.
Each phishing email is a chance for you and your colleagues to discover something new. If you only send campaigns quarterly, that’s only 4 chances a year you have to make an in-the-wild experience count. Remember, before running a phishing simulation, offer pre-training and follow-up education to assist the learner without penalizing them, recognizing that anyone can become a victim of a phishing attempt given the right circumstances.
With that in mind, here are the ingredients that every effective simulated phishing campaign should be including.
Use Diverse Phishing Scenarios
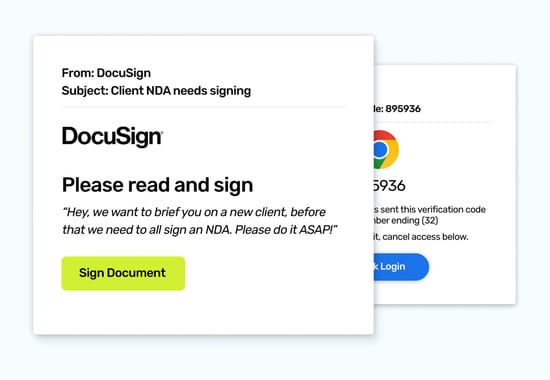
Phishing attackers are creative thinkers, willing to steal the identity of any person or service we trust in their quest to trick us into doing something they can benefit from. Therefore, having a diverse mix of fake identities is required to illustrate that almost anything we trust could be out to get us. To avoid wasted opportunities, the scenarios do need to be relevant; avoid going too far left-field, or it could be viewed as an unrealistic threat by your colleagues.
Urgent payment notifications, performance reviews, and unexpected Zoom meetings; are often seen as scams in the wild, as they are welcome in most inboxes and easily recognizable, whichever organization they arrive at. This sets up the perfect opportunity to explain why these do catch people out and how becoming too familiar can make them less careful.
Here are links to some diverse templates for inspiration: Meeting Prep, NDA Signing, DNS Disaster, Phish of Wall St, Just Browsing
Use Emotional Triggers Wizely
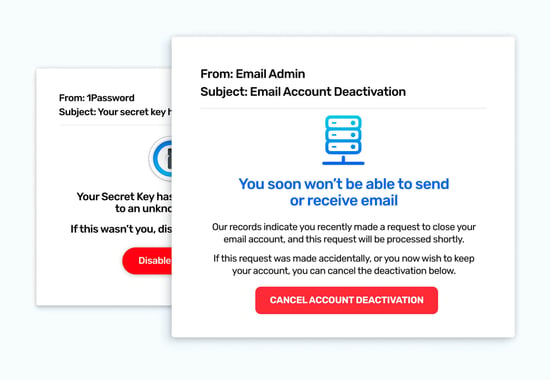
Many phishing emails sent by cyber criminals exploit human emotions to manipulate us into acting hastily. Cyber criminals aren’t trying to build trust with their colleagues, otherwise, they may take more care with who they’re upsetting! This is an important consideration for anyone running a phishing program, as the sender will always be you, and by association, your organization. A good rule of thumb is to avoid offering anything that would benefit the recipient's health, or wealth, outside of work. And take additional care with any language that might come across as more generous, caring, or sincere, than you are as an organization in real life.
There's no doubt that learning to recognize emotional manipulation is an important skill to master. By being aware of their emotional responses, employees can take a moment to verify unexpected requests, especially those designed to induce panic or urgency. But save the real low-life examples for in-person trainings to keep trust and respect among colleagues. Scammers are heartless, but phishing simulations shouldn't be!
Here are some emotion-based templates for inspiration: Slack Channels, Email Deactivation, Password Problems
These phishing templates and more available in Wizer Boost Phishing Simulation.
Authority Exposure
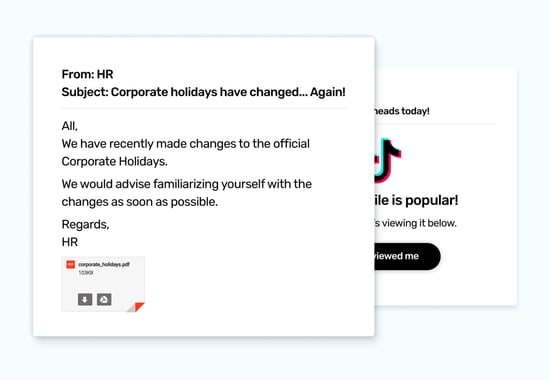
Phishing emails frequently impersonate those in authority, such as CEOs, HR, or even security administrators. It’s easy to see why they’re chosen - every organization has people in these roles, and they have the superpower of being able to ask anyone to carry out a task for them; with a good chance of it being successful.
Be sure to coordinate with HR and/or the members of the roles you'll be impersonating to avoid any ill-will or annoying interruptions for the individual being spoofed. One of our security awareness leaders shared how they successfully used these types of advanced phishing as optional exercises for their Security Champions program.
Here are some authority-based templates for inspiration: HR Mentor Program, IT Updated Policy
Time-Pressure Tactics
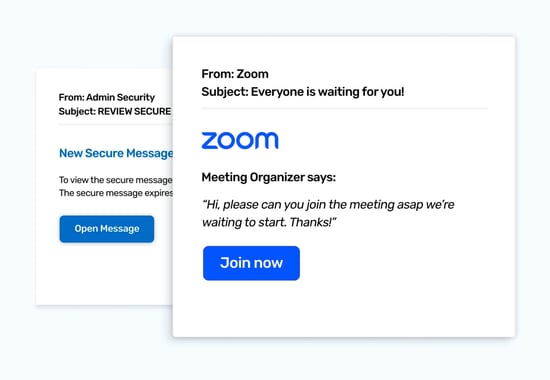
Time pressure is the scammers’ secret ingredient to compel us to act quickly. They use it so frequently because speed means less time to think - and less chance of the recipient putting the response at the bottom of their to-do list. Their last intention is for you to forget about it or for their fake web page to be reported and taken down, rendering the click they finally get as useless.
One key difference to note is that the time limits in real phishing emails and simulated phishing are often much tighter than they would be if they were genuine. Rarely, an account will suddenly be closed at the end of the day, which means highlighting this fact can help your colleagues see through the smoke and mirrors of emails designed to get a quick response.
Here are some time-based templates for inspiration: Get the Message, Zoom to the Meeting
Curiosity-Driven Clicks

Phishing templates often leverage curiosity by providing partial information and encouraging users to click on links or open attachments to learn more. We can’t blame our colleagues for being curious, it’s in our nature to want to understand what we’re presented with. In the online world the instantaneous nature of a click can almost be instinctual, it’s like opening a folded letter!
As it is becoming clear as we look at all these ingredients of a varied phishing program, explaining the illegitimate tactic, especially regarding how we respond, can be an important part of developing a sensitivity to situations that might not be genuine.
Here are some curiosity-triggering templates for inspiration: Corporate Holidays, The Corporate Video, Curious Clearout, All Eyes on You
Current & Emerging Threats
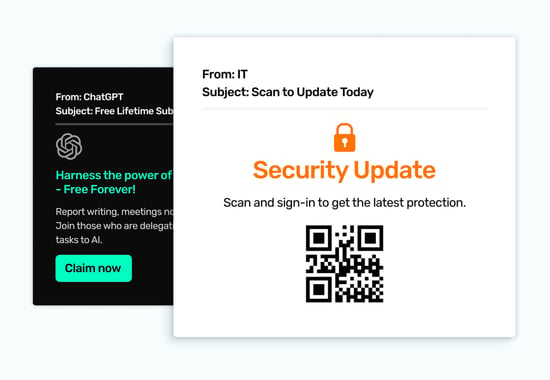
A well-rounded phishing program wouldn’t be complete without the inclusion of some simulated templates that are guided by current and future inbox threats. Keeping an eye on media reports for emerging trends that you feel could be effective against your organization and looking at the inbound threats you’re catching provide the insights you need to maintain a high level of practical relevance. These insights will benefit the emails you send to help employees stay on-their-toes for these real-life situations, too.
Utilizing in-person training opportunities is a good time to highlight some of the recent threats caught to also help drive awareness complimenting a phishing simulation. Consider it bonus points if the threat shared in a training was caught and reported by an employee to build up the importance of each employee's role in keeping everyone safer.
Here are some emerging threat templates for inspiration: ChatGPT, @Me Attack!, QR (Quite Risky) Codes!
To Wrap It up
Carrying out phishing simulations will always require some guidance and care. After all, no one is better placed to understand the culture and wider security awareness efforts than those at the helm. You could decide that you only want to focus on reducing the click rates, but we at Wizer believe taking one step back to ensure there is a strong foundation for picking each template and what it does to ensure a greater coverage of learning moments that can be experienced by all.
Ready to launch your next phishing campaign? Register now for a free 10-day trial of Wizer Boost to explore all of Wizer’s Phishing Simulation Templates and Phishing Exercises.
That's it for this month's phishing template ideas - looking for more ideas for phishing templates? Check our blog for more examples of phishing templates.
- Pre-set Phishing Calendar for the Year
- Customizable Phishing Template Editor
- 100+ Phishing Templates
- Weekly Progress Reports
.png?width=350&height=350&name=Phishing%20Template%20Dec%20Edition(1).png)

