Top 5 Must-Know phishing simulation templates - February Edition
Happy February and welcome to our new series of the Top 5 Phishing Simulation Templates brought to you by our Wizer Phishing team.
As we know, phishing simulations are one tool many organizations use to train employees how to spot phishing email attempts but running a successful phishing simulation can take work and time to find phishing simulation email examples that simulate real-life without getting redundant - so we did the work for you :). here are several phishing simulation templates that you may want to use this February.
Phishing Template : The Alert Notification
We’re told to be wary of unexpected emails, but some genuine ones are unexpected, making it hard to spot them. So rather than waiting for scammers to test how your colleagues react, it’s best to send phishing email templates, to drill for the time a real email might slip through your technical defenses.
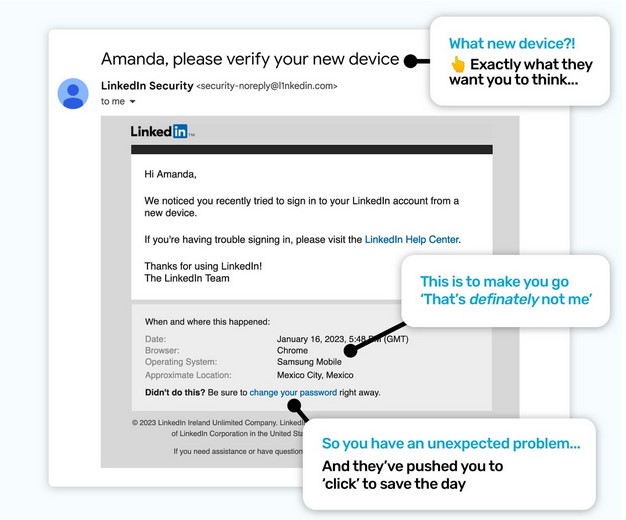
Let’s look at a genuine scenario. A scammer found your email address, and an old password in a data breach. They take those credentials and try them on LinkedIn and they work!
LinkedIn knew the login wasn’t from a location you have logged in from before, and it wasn’t from a device you use, either. So they reach out via email, to confirm it was you.
Now because LinkedIn didn’t know a scammer was going to log into your account, it’s unexpected for them. This means the email you get is unexpected, too.
And this is why these are great examples of phishing email templates, we all have no way of knowing when they will arrive, so it’s beneficial to experience the unexpected in a safe, risk-free, environment.
When we think someone has access to our account, our imagination races about what they could do. This is exactly what a scammer wants, they want us to feel pressurized because we don’t think clearly when we are.
Our advice is always to be alert for alerts! They are so popular and effective for criminals, you have to take a minute to check it doesn’t have indicators that it’s a phish.
It's crucial to help employees learn how to be aware of phishing attempts and to educate themselves on the signs of various phishing emails. One is to always be alert for alerts and don't let a phishing email put your sensitive information at risk.
Phishing Template: The Curiosity clicks
Curiosity motivates us to find out more, and online we do that by clicking.
You can’t browse the internet without someone trying to get you to click and visit their content. They entice us with offers we can’t refuse, worries we want to fix, and curiosity we can’t ignore.
One example of a curiosity click is an instance where we see a link to a news article saying ‘Your iPhone is unsafe unless you change this setting NOW’.
Do we keep on scrolling or do we want to see if our iPhone is unsafe? The trick they play is… we won’t know for sure unless we click.
Scammers use curiosity in their phishing emails; they give part of a story and hope we want to find out more. Phishing email templates should include a collection of curiosity-triggering messages that almost anyone could fall for, making them an important part of any phishing simulation solution.
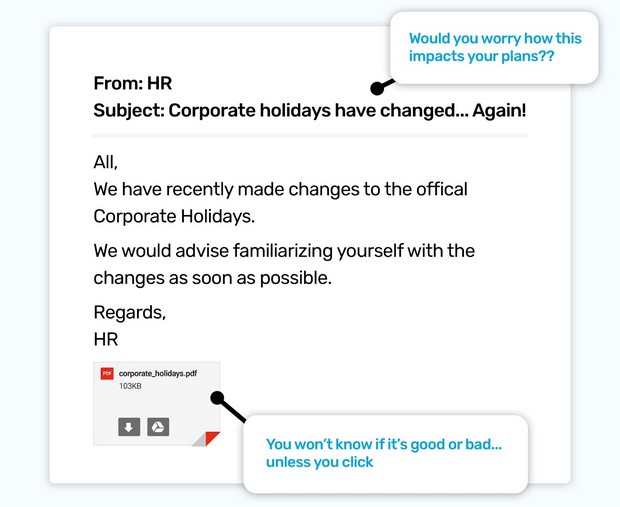
Take a look at the subject line in the phishing simulation example above; ‘Our corporate holidays have changed... Again!’ combined with the email also containing an attachment.
We might want to see how the changes affect the time-off we’ve booked or see if there are more holidays now… or less! In short, if we want to see how the holidays have changed, we have to open the file.
Whatever the reason, scammers know we all have to keep up with the changes our employer makes. By saying there's been a change, they can make us click a link, or open a document, to find out what the change is.
Help your employees learn to identify and guard against this tactic by taking extra care when there has been a change to something that affects everyone with clear protocols and processes that are adhered to. Time-off policies; sickness; WFH; are all common topics for scammers to choose from.
A real-life story training based on this tactic to share with employees is here.
Phishing Template: The Time Crunch
You’re late for work, and you rush out of the door and jump in the car. As you reach the first junction, you remember you’ve left a folder you needed on the kitchen table, argh! Why does this always happen at the worst time?
Well, it happens because it is the worst time! Time pressures make us more prone to errors in memory, and thinking.
Scammers are always looking for ways to pressurize us. They know the more time we have to think, the more likely it is we will notice something is not right.
With no pressure of time, we may catch that the email address is wrong, or the wording could remind us of a scam we’ve seen in a security training video.
And this is all on top of dropping into our busy day because it’s rare we only have one email to read, and one task to concentrate on. A scammer's pressure is added on top of what we are already facing.
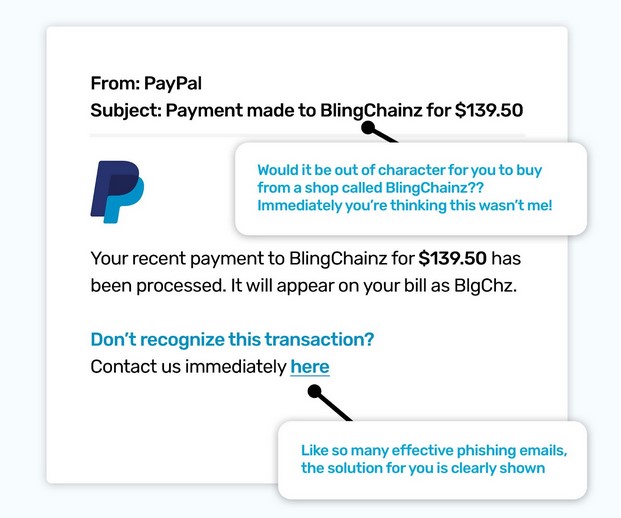
To add time pressure, scammers love to alert us to a big problem, one that would be stressful to ignore. An email account is closed; an unexpected payment leaving your account; or even an urgent request from your CEO.
These phishing email examples want action right away to push us to focus on solving the problem so we don’t have time to step back and check if the request is genuine.
Remember that no matter how urgent something is, it can always wait a few extra seconds. Check the email address, and that any links included, are legitimate. And these are all messages you can reinforce when you include time-pressure topic emails in your simulated phishing emails.
Phishing Template: The Panic Button
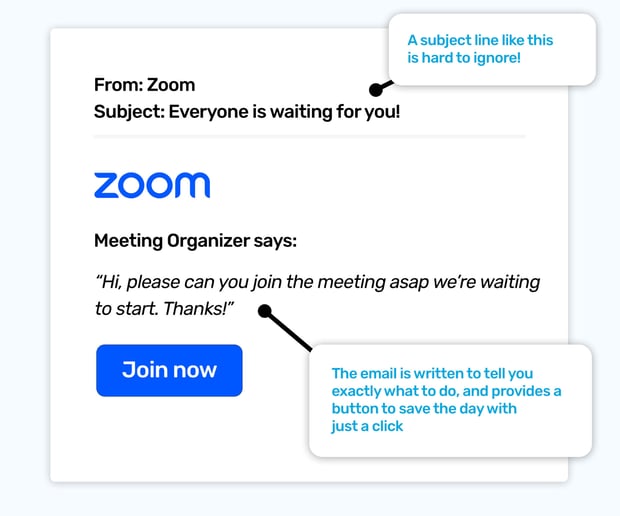
It’s clear as we look at different phishing awareness email templates, that cybercriminals often target our emotions to make us act from an emotional state instead of a logical state. So it’s not a surprise they don’t have a problem with trying to make us panic a little, too. They might say an account of ours will be closed soon, or someone has logged into an account of ours, or as this phishing simulation example shows, you’re missing a planned Zoom meeting that’s just started.
Panic is like having a problem to solve, we want the reason we’re panicking to not be there any longer. So to remove the panic of missing the start of a meeting, we have to log in and join it as soon as we can!
In that situation, we aren’t able to start checking our calendars and look back through our emails. It’s far easier, and quicker, to just join and worry about why it was missed later.
Panic is a powerful tool for cybercriminals to use. Not only does it stop us from leaving the email to get forgotten about, but it also puts us in a state where making security decisions harder, too.
By understanding how scammers manipulate us, we can learn to recognize when we’re being put under sudden pressure, and give ourselves extra time to check we aren’t being tricked.
Cybercriminals don’t care about what they have to say to put pressure on us, they might use topics such as termination or other cruel subjects.
When sending phishing simulation templates it’s good to remember these are your friends and colleagues too! Making them go ‘whoops’ is ok when it leads to an opportunity to learn, but we would steer clear of sending anything that might upset them and weaken the security culture you’re fostering.
The below real-life story demonstrates how curiosity and panic can work together as a phishing tactic.
Phishing Template: The Performance review
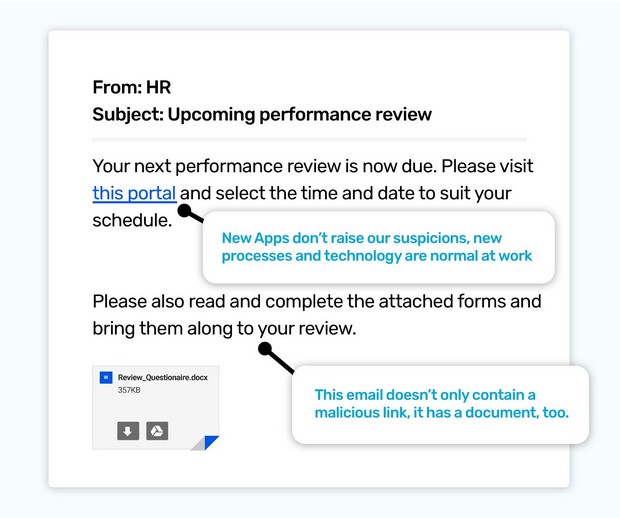
Have you ever wondered if how fast you respond to your performance review is part of your performance review?! It's probably not, but then again if you ignore it, that’s probably not a good thing.
As we’re learning, cyber criminals don’t want to be ignored when they land in an inbox, and they like to select pretexts (the subject matter and story within an email) that they know we have to act upon.
This is why a performance review email is very popular, it’s very likely to get attention.
Performance reviews, in real life, can be hard to predict the timing of. They may follow a rigid structure, but they may also be ad hoc, and each time it comes around it feels out of the blue.
But even if you know with certainty when your next review is due, things change. And we can easily convince ourselves there must be a reason behind it, and accept changes without question, especially when there’s authority involved.
Another danger of performance reviews is as well as timing adjustments, the format and documentation can alter, too. We might get a PDF to read, or we might have to log into a new portal or select a date, it’s not a given we will know what we will be asked to do.
Whilst we can’t advise you to ignore all performance review emails we can help you to approach them with care. No matter how quickly you want to reply or read what’s been sent, accept these types of emails are sent by scammers. Although authority can make us reluctant to question things, it’s always best to reach out to the sender directly if you have any concerns. That could be via a call or an internal messaging service.
Note: Always make sure you use performance review phishing email templates wizely. Sometimes the timing of them could be counterproductive to the learning process, such as sending them out when lay offs have been announced or when genuine performance reviews are underway.
That's it for this month's phishing template ideas - see you next month!
Ready to launch your next phishing campaign? Register now for a free 10-day trial of Wizer Boost to explore all of Wizer’s Phishing Simulation Templates and Phishing Exercises.
Top 5 Must-Know Phishing Simulation Templates - March Edition
- Pre-set Phishing Calendar for 2023
- Customizable Phishing Template Editor
- 100+ Phishing Templates
- Weekly Progress Reports