5 Must-Use Phishing Simulation Templates for January 2025
As the holiday rush subsides and the new year begins, many employees return to work with resolutions to be more productive. Cybercriminals, however, see this period as an opportunity to exploit post-holiday complacency. January is a prime time for phishing attacks, especially as organizations prepare for annual reviews, process year-end financials, and engage with new tools or services.
With inboxes still overflowing and attention fragmented, vigilance remains critical. These five phishing simulations are perfect for keeping your team sharp against evolving cyber threats.
Download these phishing templates for your in-person security awareness training materials!
Robot Review

Scenario: Employees receive an email from "HR" with the subject line: "Your Automated AI Performance Review Has Landed!" The email informs them that an AI-generated review of their performance over the past six months is ready and provides a button to "View Review."
The Hook: This simulation leverages the rising prevalence of automation and AI-driven services. Performance reviews are already a sensitive topic, and the introduction of AI as the evaluator triggers curiosity. Employees are likely to wonder, "What criteria can AI even judge me on?" and "How has it judged me?" To ease anxiety, the email includes a line clarifying that this is just a test and won’t appear on any records, encouraging clicks by downplaying any potential consequences.
Real-world risk: Clicking the button could lead to a fake HR portal designed to harvest employee login credentials or personal information.
Tips for spotting this phish:
- Double-check the sender’s email address for inconsistencies.
- Confirm with HR directly if your organization uses AI for performance reviews.
- Never click links in unexpected emails; instead, access performance reviews through your organization’s secure HR platform.
Data Dilemma
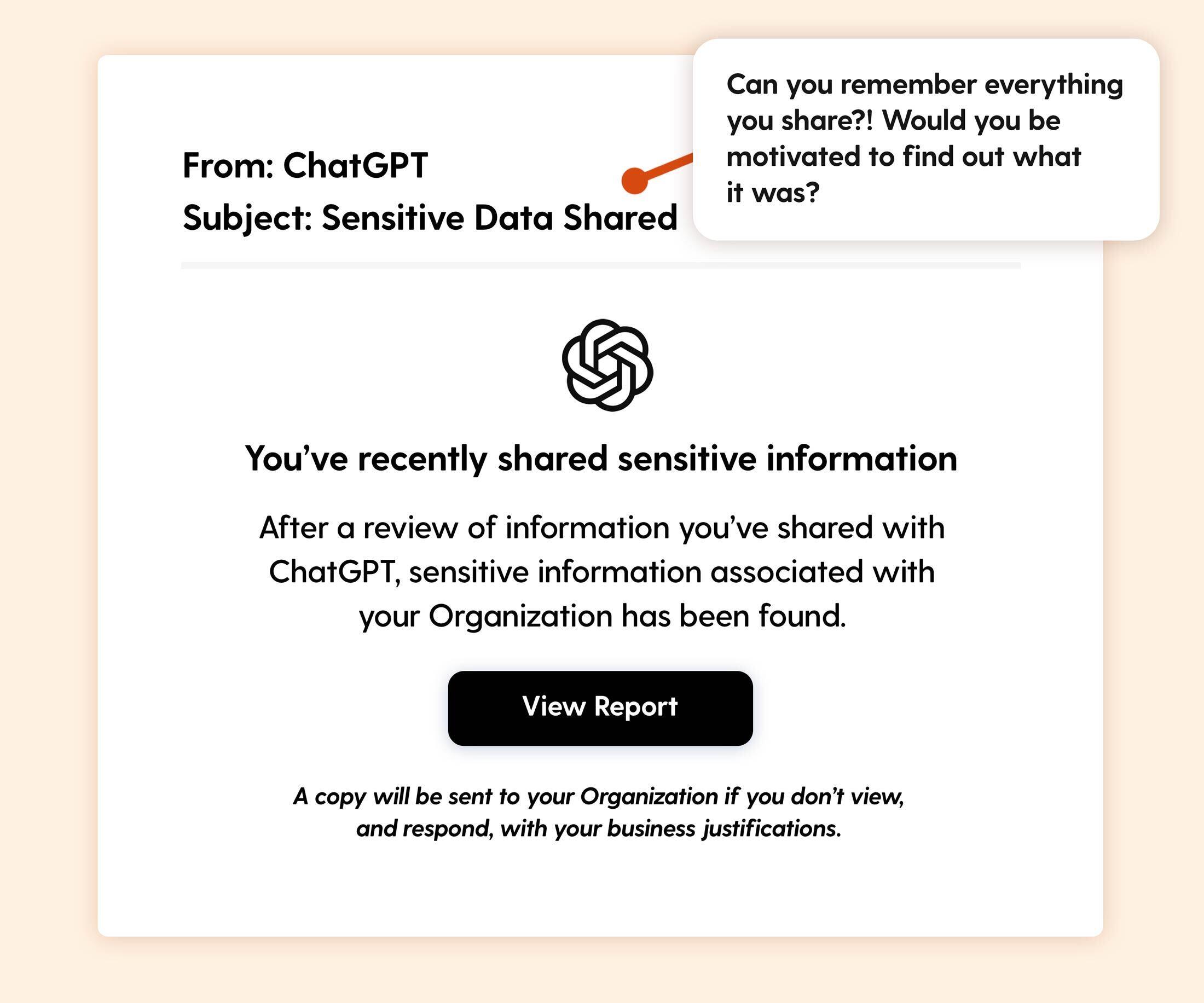
Scenario: An alarming email from "ChatGPT" claims that sensitive data you shared with the tool has been flagged as a potential security risk. It warns that a report will be sent to your organization unless you review and justify your actions immediately.
The Hook: This phishing email employs two powerful coercion techniques. First, it preys on the common business worry that sensitive information might have been shared with AI tools like ChatGPT. This plays into a natural behavior where users think, "If I can type it into a document, I can type it into a chatbot." The second technique taps into curiosity: even if you haven’t shared sensitive data, you might begin to wonder, "Did I use another service that relies on ChatGPT capabilities?" With the platform integrating more deeply into ecosystems like Apple’s, this doubt feels plausible. Finally, time pressure is introduced by warning that the issue hasn’t yet been reported to your organization but will be if you don’t respond.
Real-world risk: The "View Report" button could redirect users to a malicious website designed to steal login credentials or infect devices with malware.
Tips for spotting this phish:
- Verify with your IT department if such monitoring exists.
- Always access trusted tools directly, like this one from ChatGPT, rather than through email links.
- Check for subtle grammatical or stylistic errors in the email’s content.
Resisting change
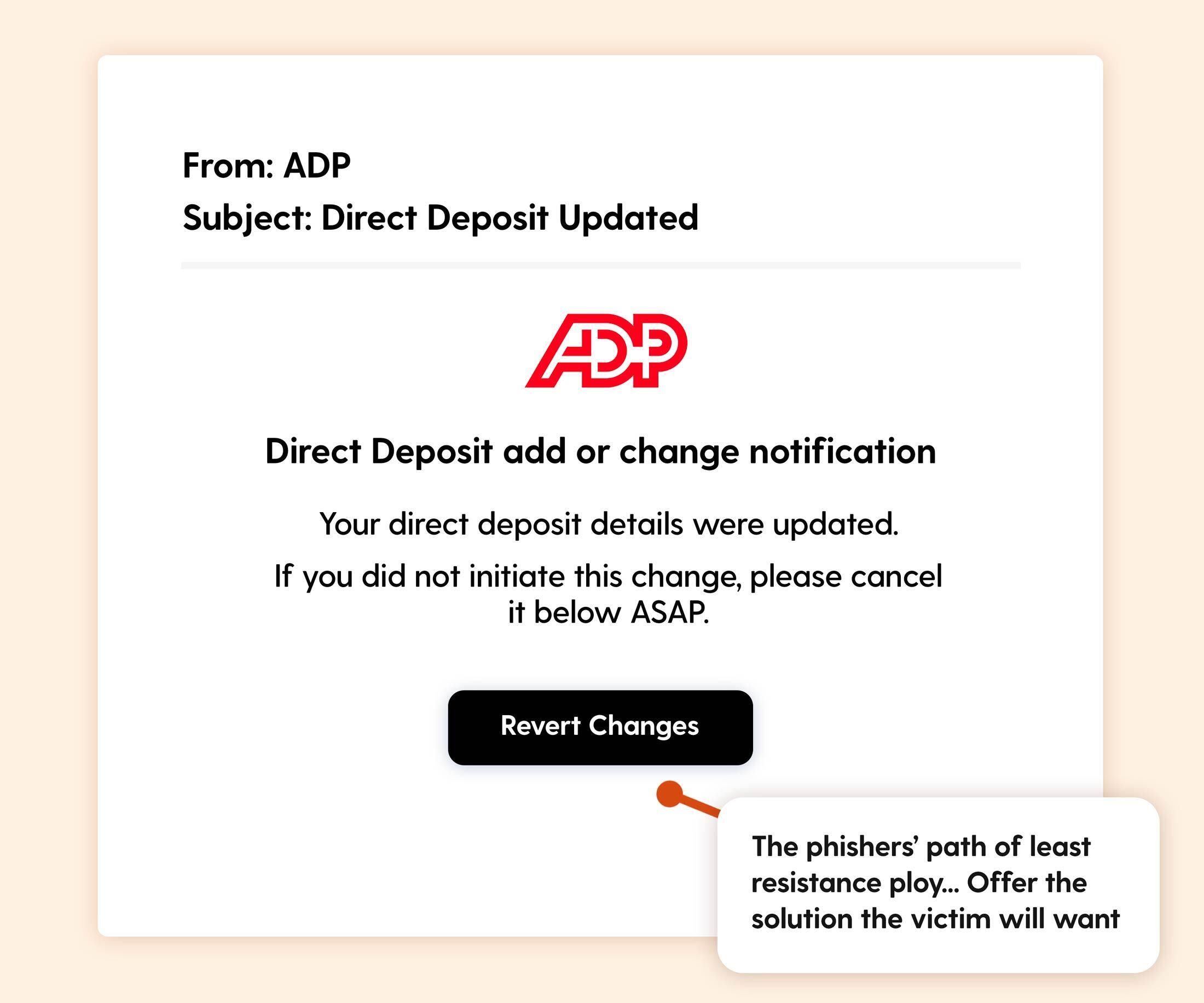
Scenario: An email from "ADP" informs the recipient that their direct deposit details have been updated. If they did not initiate this change, they are urged to click "Revert Changes" immediately.
The Hook: This type of phishing email follows a simple but effective strategy: it tells a lie that raises concern (your direct deposit details were changed without your consent), then immediately offers the exact solution you’re hoping to see—a button to reverse the issue. This approach creates a natural emotional and cognitive "groove" for the recipient to follow. The combination of fear, relief, and urgency often leads to impulsive clicks.
Real-world risk: Clicking the link could lead to a spoofed payroll portal designed to capture banking details or login credentials.
Tips for spotting this phish:
- Look for unusual language or formatting in the email.
- Contact your payroll department directly to confirm any changes.
- Avoid clicking on urgent calls to action; verify information through official channels.
Mystery Invite
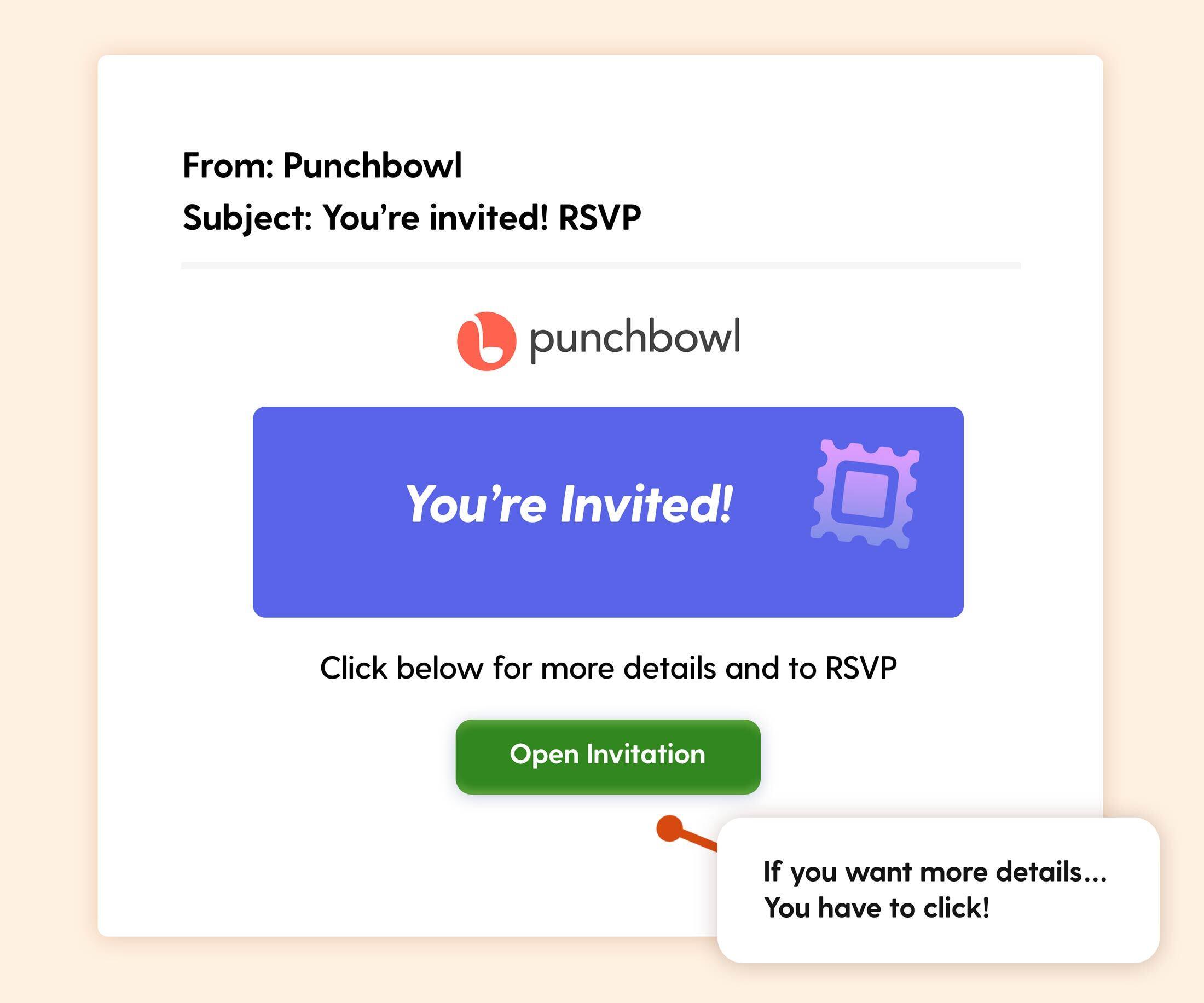
Scenario: An invitation from "Punchbowl" invites the recipient to RSVP to an event. To view more details or confirm attendance, they must click "Open Invitation."
The Hook: At first glance, this email seems innocuous. Who wouldn’t want to learn more about a surprise invitation? However, the real danger arises if the link requests the recipient to sign in via their trusted single sign-on (SSO) credentials. This seemingly harmless step could initiate a risky process where attackers harvest login details under the guise of verifying the invite sender.
Real-world risk: Clicking could direct the recipient to a fraudulent site mimicking an event platform, where they might be tricked into providing sensitive details, including their SSO credentials.
Tips for spotting this phish:
- Verify the sender’s email address and domain.
- Check with colleagues or event organizers if the invitation is unexpected.
- Avoid entering login credentials on unfamiliar sites; access known platforms directly instead.
Platform Purgatory
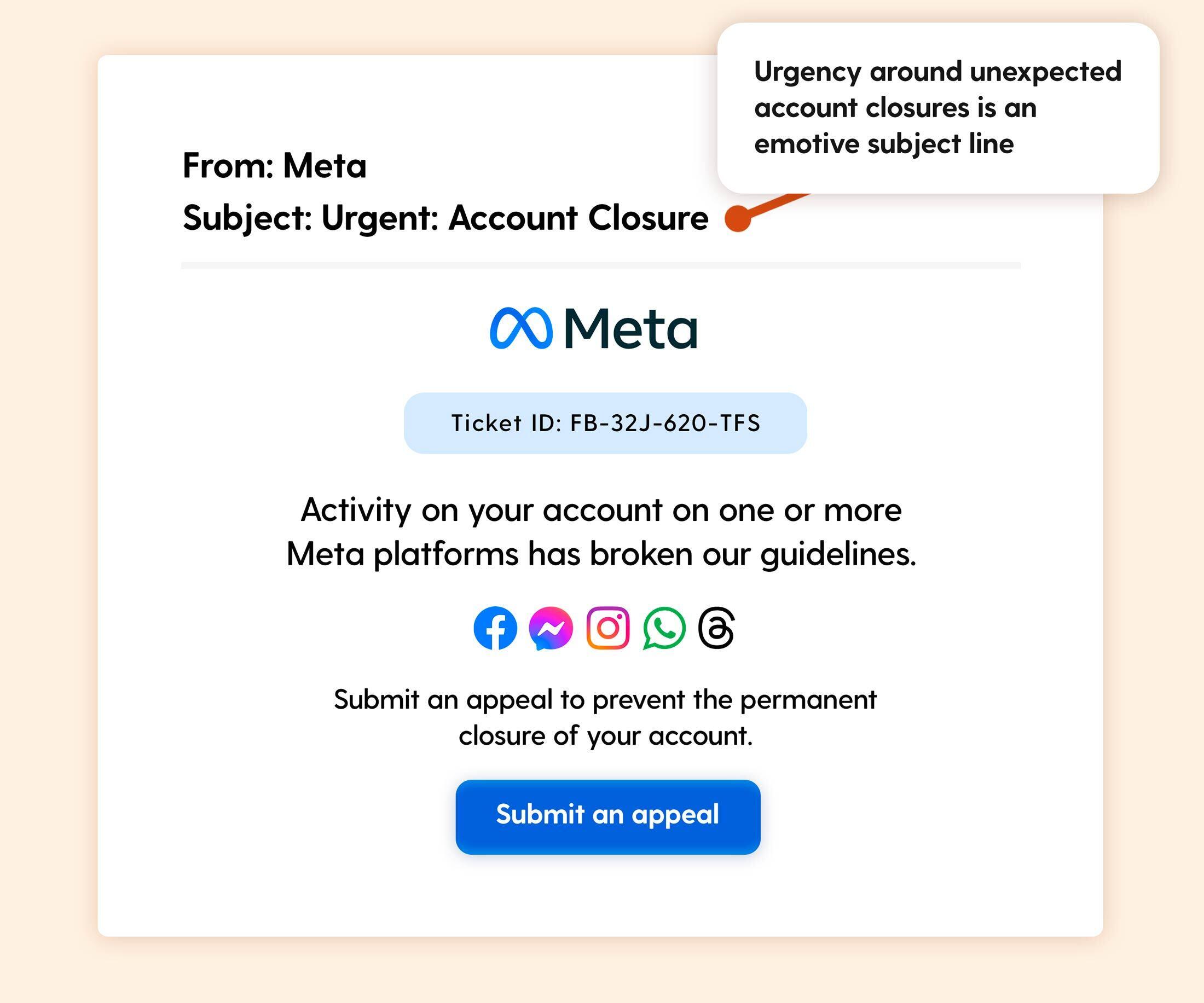
Scenario: An email from "Meta" warns the recipient that their account has violated platform guidelines and faces closure unless an appeal is submitted immediately. A "Submit an Appeal" button is provided.
The Hook: This phishing email cleverly broadens its appeal by referencing activity on "one or more Meta platforms." This ambiguity increases the likelihood of engagement, as recipients using any Meta service (such as Facebook, Instagram, or WhatsApp) may fear they’ve unknowingly breached guidelines. To heighten the urgency, the email warns that inaction will lead to account closure, prompting users to click and investigate further.
Real-world risk: Clicking the button could lead to a fake Meta login page designed to steal credentials or install malware.
Tips for spotting this phish:
- Inspect the sender’s email address for accuracy.
- Log in directly to Meta platforms to verify account status.
- Be wary of emotionally charged subject lines designed to elicit fear.
Stay Vigilant in the New Year
Phishing attacks evolve constantly, and cybercriminals exploit trust, urgency, and curiosity to trick even the most cautious users. Integrating these phishing scenarios into your training programs will keep your team vigilant and prepared for the tactics they’re likely to encounter in 2025.
Want to explore more phishing simulations? Browse our blog for additional templates, and stay ahead of cyber threats with our curated training resources.
Ready to level up your organization’s cybersecurity? Register for a free trial of Wizer Boost to access our full library of phishing templates and exercises.
- Interactive Phishing Response Game
- Short, Randomized Challenges
- Encourage Proactive Responses
- Go Beyond A Typical Simulation
.png)