Top 5 Must-Know Phishing Simulation Templates - July 2024
This month's phishing attack simulation templates showcase how scammers use common work scenarios – from breach alerts to customer loyalty rewards – to trick us into clicking malicious links. Give your team the knowledge they need to stay alert and outsmart the phishers.
Download these phishing templates for your in-person security awareness training materials!
Breach Bait
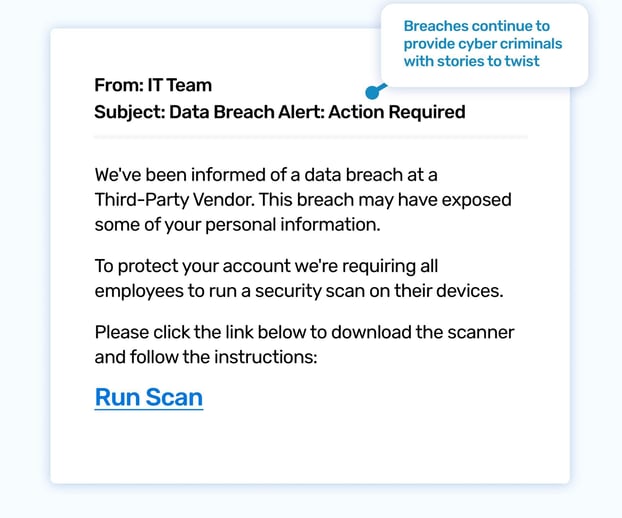
You're wrapping up work when an urgent email from IT Security appears in your inbox: "Data Breach Alert." Your stomach drops. A third-party vendor has been breached, and your information might be compromised. The email asks you to download a security scanner immediately. Panic sets in. This doesn’t seem like a request you can ignore...
This simulated phishing attack preys on our reacticons data breaches and the sense of urgency that comes with protecting our personal information. The email appears legitimate, referencing a known third-party vendor and emphasizing the need for immediate action. The attached "security scanner" is actually malware designed to steal sensitive data.
This template is especially relevant in today's online world where third-party breaches are becoming more common. It highlights the importance of verifying the legitimacy of security alerts and downloading software only from trusted sources.
Access all areas
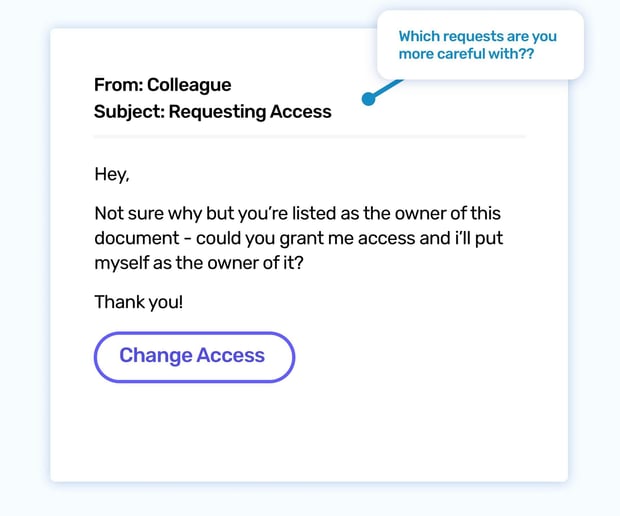
An email from a colleague pops up: "Requesting Access to a document you created." They can't access a file and are asking you to grant them ownership. Seems harmless enough, right? You click the link they provide, eager to help... but wait, something's not right.
This phishing attack simulation exploits our trust in our colleagues and our willingness to help. The email appears casual and friendly, masking its malicious intent. The link leads not to a shared document, but to a fake login page designed to capture your credentials.
Phishing attacks are becoming increasingly sophisticated, often impersonating people we know and trust. This scenario highlights the importance of scrutinizing even seemingly harmless requests, especially those involving links or logins. When in doubt, reach out to your colleague directly to confirm the request. triggered??
Curiosity Trap
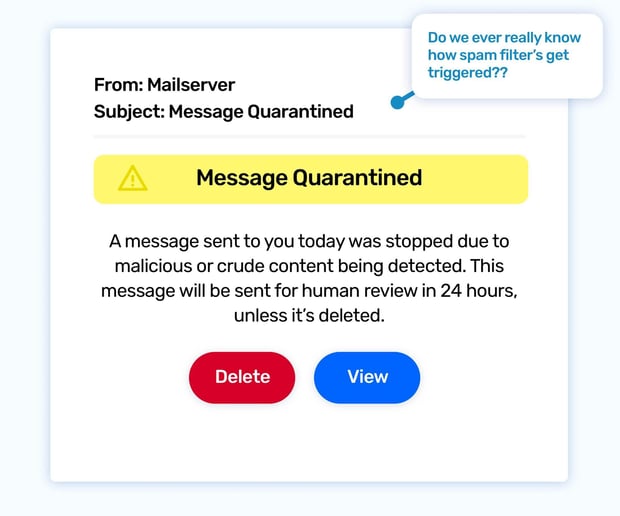
You open your inbox and notice an email from Microsoft or Google, your trusted email provider. The subject line reads, "Prevented Spam / Quarantined messages." Relieved that a potentially dangerous email has been stopped, you click to review the details. Out of curiosity (or perhaps a touch of paranoia), you decide to click the "Release" button, thinking it might be a false alarm...
This phishing simulation exploits our trust in security measures and our desire to stay informed. The email cleverly mimics a legitimate notification from your email provider, lulling you into a false sense of security. The "quarantined" message is actually the bait. Clicking to release it triggers a download of malware or leads you to a malicious website.
Even spam filters aren't foolproof. Phishers are constantly evolving their tactics to bypass these protections. This scenario underscores the importance of exercising caution even with emails that appear to come from trusted sources. Remember, never click links or download attachments from emails unless you are absolutely sure of their legitimacy. When in doubt, double-check with the sender through a different channel.
Reverse of Fortunes
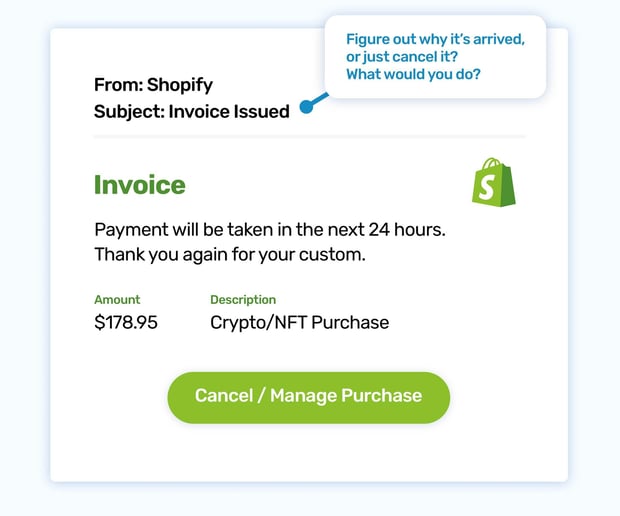
You open your inbox and spot an email from Shopify with the subject line "Receipt for your recent purchase." A wave of confusion washes over you. Did you buy something recently? Did you forget about an old subscription? Your pulse quickens. You scan the email for details, your eyes drawn to a button inviting you to cancel the order. Relief washes over you—you can still stop the payment! Without thinking, you click the button, eager to fix the problem...
This phishing simulation capitalizes on our fear of unauthorized charges and our desire for quick resolutions. The email appears legitimate, using Shopify's branding and a seemingly innocent subject line. The "Cancel Order" button is the bait, leading unsuspecting users to a fake Shopify website where they are prompted to enter their login credentials and credit card information to "cancel" the purchase.
This scam preys on our natural reactions to unexpected charges, triggering a sense of urgency that overrides our usual caution. It highlights the importance of carefully scrutinizing emails, even those that appear to come from reputable companies. Remember, legitimate businesses rarely ask for sensitive information via email.
Perilous Prizes
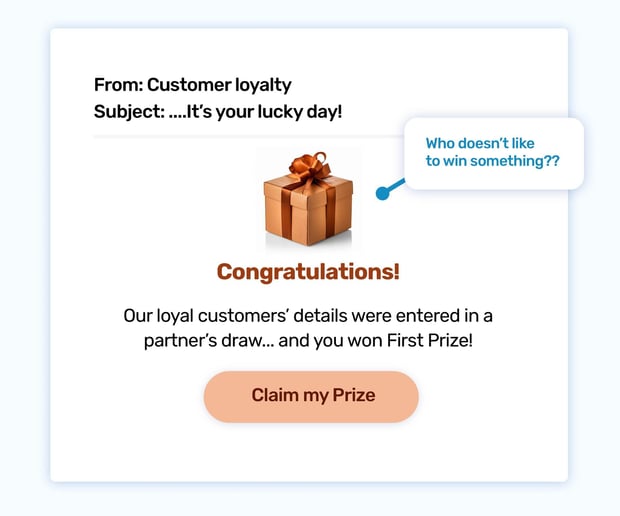
You're scrolling through your inbox when a colorful email catches your eye. "[Company Name]?" you think. "I don't remember entering any giveaways..." But curiosity gets the better of you, and you open the email. It's a congratulatory message announcing that you've won a fantastic prize! Excitement bubbles up inside you. This could be your lucky day! You eagerly click the link to claim your prize...
This phishing simulation preys on our natural desire for rewards and recognition. The email uses the branding of a familiar company, making it seem more legitimate. The promise of a valuable prize triggers a rush of excitement, clouding our judgment and making us more likely to click without thinking. The link, however, leads to a fake website designed to steal your personal information.
While winning a prize is always exciting, it's important to remain vigilant. Phishing scams often use the lure of freebies or special offers to trick people into giving away their sensitive information. This scenario reminds us to approach unexpected "wins" with caution, verifying the legitimacy of the offer before taking any action.
Ready to launch your next phishing campaign? Register now for a free 10-day trial of Wizer Boost to explore all of Wizer’s Phishing Simulation Templates and Phishing Exercises.
That's it for this month's phishing template ideas - looking for more ideas for phishing templates? Check our blog for more examples of phishing templates.
- Interactive Phishing Response Game
- Short, Randomized Challenges
- Encourage Proactive Responses
- Go Beyond A Typical Simulation
.png)

