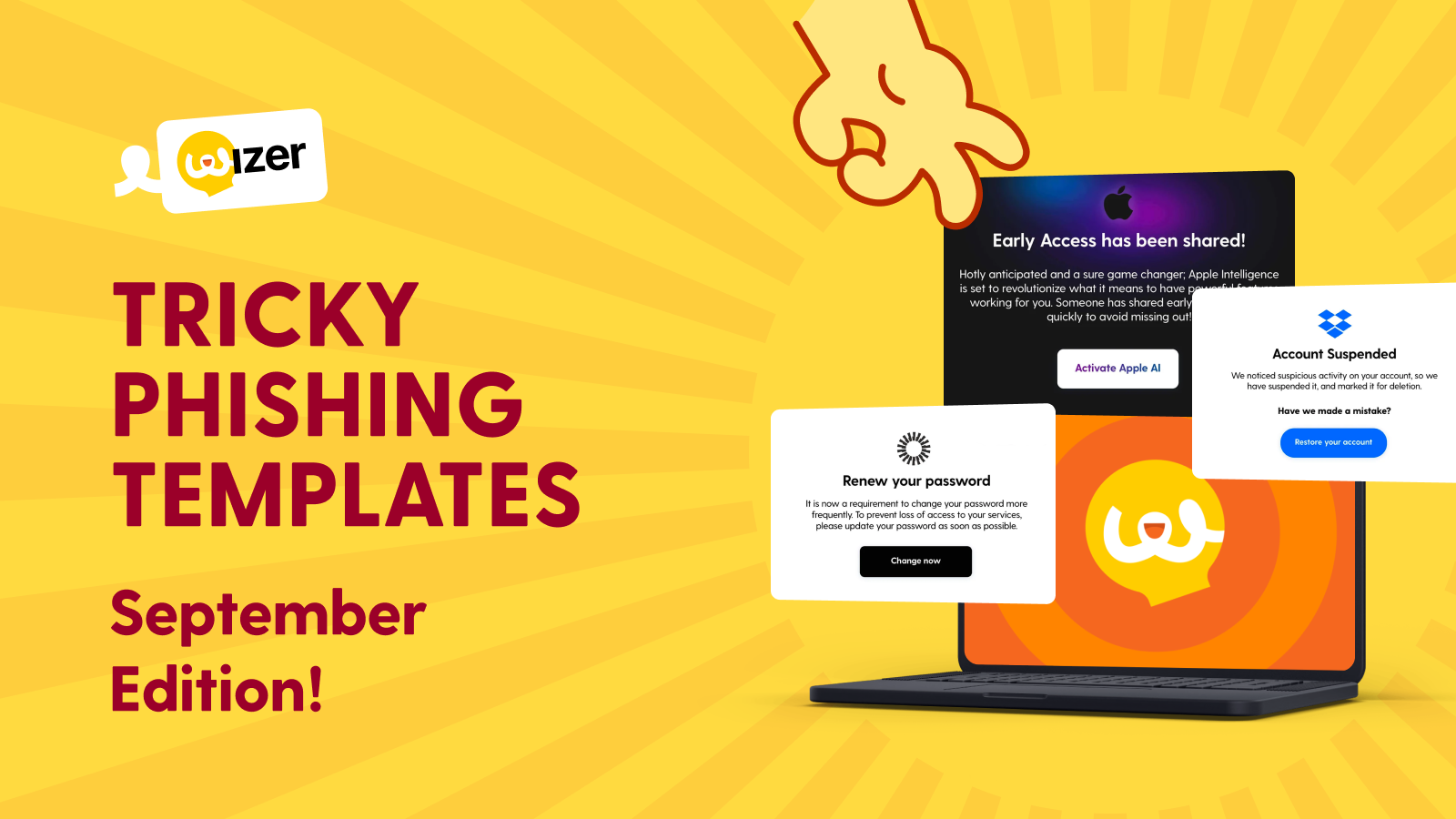
Top 5 Must-Know Phishing Simulation Templates - June 2024
Phishing attacks are showing fewer red flags than they used to, helping them to hide in the communications of our increasingly busy digital lives. This month's simulations showcase how scammers use everyday scenarios – from package deliveries to software updates – to trick us into clicking malicious links. Let's equip your team with the knowledge they need to stay alert and outsmart the phishers.
Download these phishing templates for your in-person security awareness training materials!
Confidential Bait

It's Monday morning, and you're sifting through the usual deluge of emails. One from Dropbox catches your eye: "File Shared: 'ProjectX_Financial_Report_Q2.xlsx'." Curiosity piqued, you pause. Project X is confidential, and you weren't expecting this report so soon. Did someone accidentally share it early? Or is something else going on? Eager to get ahead of the game, you click the link to download the file, hoping to get a sneak peek at the numbers....and got more than you bargained for.
This phishing attack preys on our natural curiosity and the desire to be in the know. It uses the familiarity of Dropbox, a trusted file-sharing platform, to lull us into a false sense of security. The file name suggests confidential information, making it even more tempting to click. By simulating this type of attack, you can teach your employees to be cautious of unexpected file shares, especially those containing sensitive information. Always verify the legitimacy of the share through other channels (e.g., by contacting the sender directly) before downloading any files.
Delivery Detour
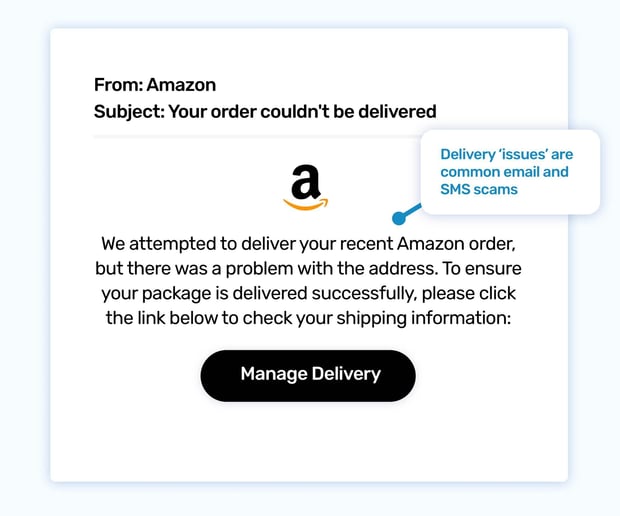
You're eagerly awaiting a package from Amazon. Then, you receive an email saying they couldn't deliver it due to an address issue. Panic sets in. You don't want your package to get lost! You quickly click the link to update your details, not realizing you're falling for a phishing scam.
This template preys on the anticipation and excitement of online shopping, especially during busy periods like holidays. It uses the trusted Amazon brand to appear legitimate and creates a sense of urgency to update information quickly.
Disruption Deception

You're heads-down in a focused work session when an email from Facilities Management pops up. The subject line, "Important Notice: Upcoming Building Maintenance," grabs your attention.
You're immediately curious about how this might impact your day. Will your office be affected? Will the noise be disruptive? Eager to find out the details and plan accordingly, you click on the attached "Building_Maintenance_Schedule.pdf".
This phishing attack preys on our natural curiosity and the desire for information that directly affects our work environment. The email uses the guise of a routine communication from a trusted source to appear legitimate. By creating a sense of uncertainty and potential disruption, it triggers a need to know more. The attachment, disguised as a harmless schedule, serves as the bait to deliver malware or compromise credentials.
Holiday Hijack

The thought of sandy beaches and warm sunshine is getting more tempting by the day. Then an email from American Airlines pops up, offering an exclusive vacation discount code. Your heart skips a beat. This could be the perfect opportunity to book that trip you've been eyeing! Without hesitation, you click the link to "Book your flight now," eager to snag the deal before it's too late.
This phishing attack preys on our desire for a bargain and our anticipation of the vacation season. The email creates a sense of urgency with the "limited time only" offer, pushing us to act quickly. The promise of a discounted dream vacation can easily overshadow our caution, making us more likely to click on a malicious link without scrutinizing the details.
Upgrade Ultimatum
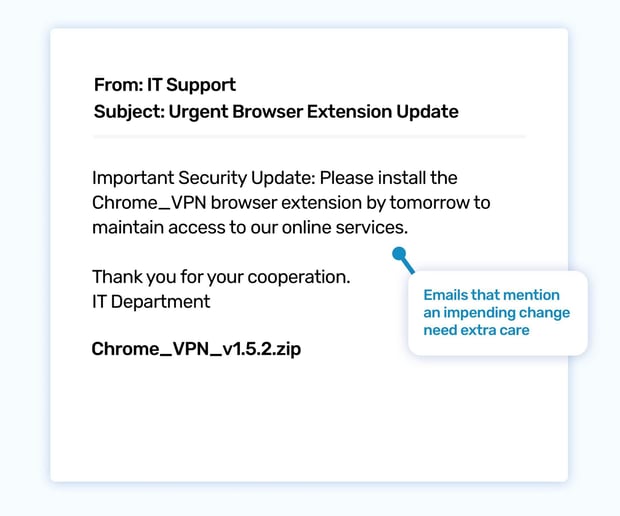
You're racing against the clock to meet a project deadline, relying heavily on your suite of cloud-based tools. Then, an urgent email from IT lands in your inbox: "Urgent Browser Extension Update Required." The deadline is looming, and the email warns of "restricted access" to critical platforms if you don't comply. Panicked, you click the link to install the extension, fearing a sudden disruption to your workflow.
This phishing attack preys on our dependence on digital tools and the fear of missing deadlines or losing access to crucial resources. The email's tone of authority and urgency compels immediate action. By simulating this type of attack, you can teach your employees to be cautious of unsolicited software installations, even when they appear to come from a trusted source like the IT department. Encourage them to verify update requests through official channels before installing anything new.
Ready to launch your next phishing campaign? Register now for a free 10-day trial of Wizer Boost to explore all of Wizer’s Phishing Simulation Templates and Phishing Exercises.
That's it for this month's phishing template ideas - looking for more ideas for phishing templates? Check our blog for more examples of phishing templates.
- Interactive Phishing Response Game
- Short, Randomized Challenges
- Encourage Proactive Responses
- Go Beyond A Typical Simulation
.png)