5 Phishing Simulation Email Templates To Refresh Your Security Awareness Training
Cybercriminals never take a break, and neither should your security awareness efforts. March brings new phishing threats that exploit trust, urgency, and curiosity. These phishing email templates are designed to help assess employees' ability to recognize and respond to real-world threats, testing their awareness of social engineering tactics, suspicious links, and credential-stealing schemes. By incorporating these simulations, organizations can better understand their security vulnerabilities and reinforce good cybersecurity habits.
Download these phishing templates for your in-person security awareness training materials!
Lyft Lure

Scenario: Cybercriminals never take a break, and neither should your security awareness efforts. March brings new phishing threats that exploit trust, urgency, and curiosity. These phishing email templates are designed to help assess employees' ability to recognize and respond to real-world threats, testing their awareness of social engineering tactics, suspicious links, and credential-stealing schemes. By incorporating these simulations, organizations can better understand their security vulnerabilities and reinforce good cybersecurity habits.
The Hook: The idea of free rides, especially those covering up to 30 miles each, is incredibly tempting. Even employees who rarely use Lyft might be inclined to claim the offer “just in case.” The balance of believability makes this scam dangerous—it’s not an absurd giveaway, but it’s still generous enough to be enticing.
Real-world risk: Clicking the link may lead to a phishing page that asks for login details or credit card information.
Tips for spotting this phish:
- Too-good-to-be-true offers are common lures—always verify through official sources.
- Check the sender’s email for subtle misspellings or inconsistencies.
- Avoid clicking promotional email links—visit the official app or website instead.
Flight Fraud
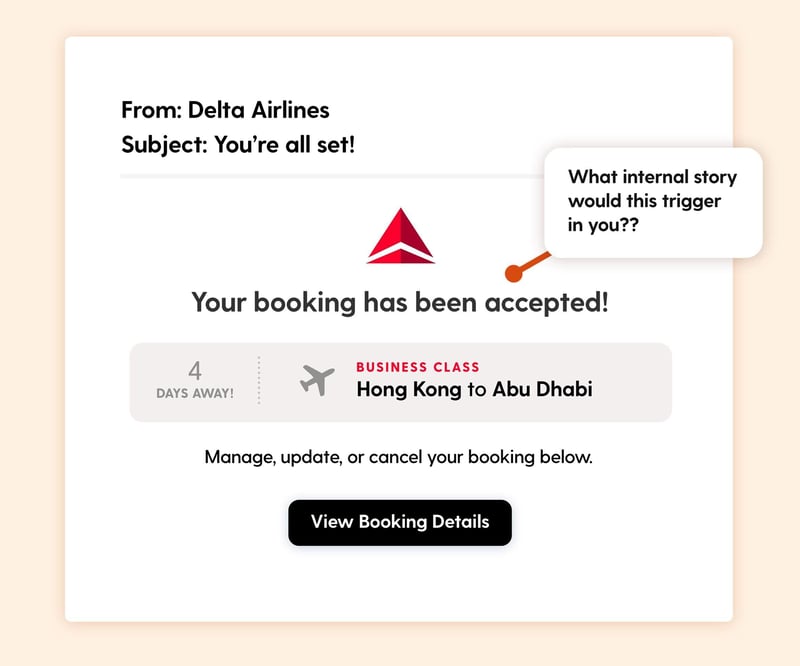
Scenario: Employees receive an email confirming a business-class flight booking to Dubai that they never made. The flight is set to depart in just four days, creating urgency. A “View Booking Details” button invites them to check more information or cancel.
The Hook: The shock of receiving a high-cost booking they didn’t make will make most people immediately want to investigate. The lack of information—who booked it, how it happened—creates an urgent need to click.
Real-world risk: Clicking the link could lead to a fake airline website designed to steal login credentials or credit card details.
Tips for spotting this phish:
- If you suspect fraud, log into your airline account directly, not through email links.
- Look for missing booking reference numbers or suspicious sender addresses.
Geek Squad Gimmick

Scenario: Employees receive an email stating that their Geek Squad trial has ended, but a 12-month subscription renewal for $288 is about to be charged. The email includes a big “Cancel Payment” button for those who don’t want the charge.
The Hook: Many people sign up for trials without remembering, or they fear they may have unknowingly activated a service during a checkout process. Seeing an upcoming charge for an unwanted service creates panic, driving people to click without second-guessing.
Real-world risk: Clicking the “Cancel Payment” button could lead to a phishing site where victims enter sensitive financial information or login credentials.
Tips for spotting this phish:
- Verify subscriptions by logging into the provider’s website directly.
- Be wary of emails demanding immediate action for unfamiliar charges.
- Avoid clicking “cancel” links in emails—contact customer service directly if needed.
Location leak
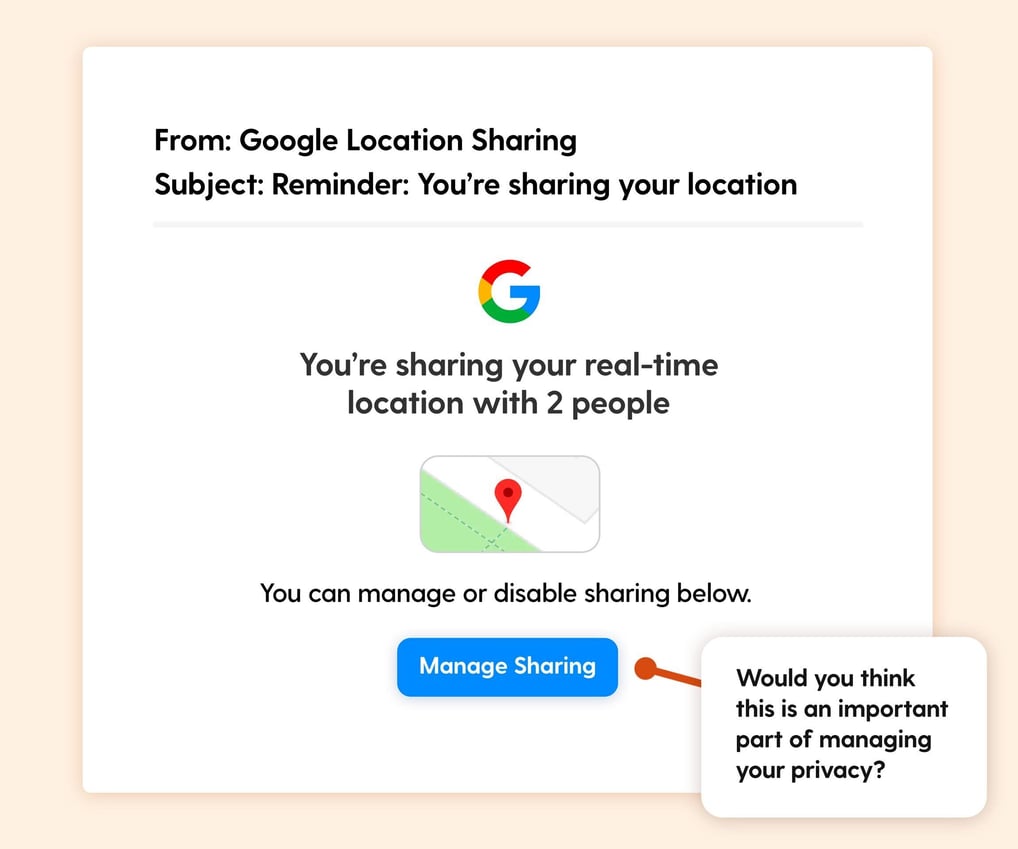
Scenario: Employees receive an email warning that their real-time location is being shared with two unknown individuals. The email provides a “Manage Sharing” button to adjust permissions.
The Hook: This scam plays on privacy concerns and curiosity. The lack of information on who the two people are triggers an immediate need to check and potentially revoke access.
Real-world risk: Clicking the button may lead to a fake Google login page, tricking employees into entering their credentials.
Tips for spotting this phish:
- Beware of vague security alerts that don’t mention specific account details.
- Enable multi-factor authentication (MFA) to reduce the risk of unauthorized access.
AI Policy Phish
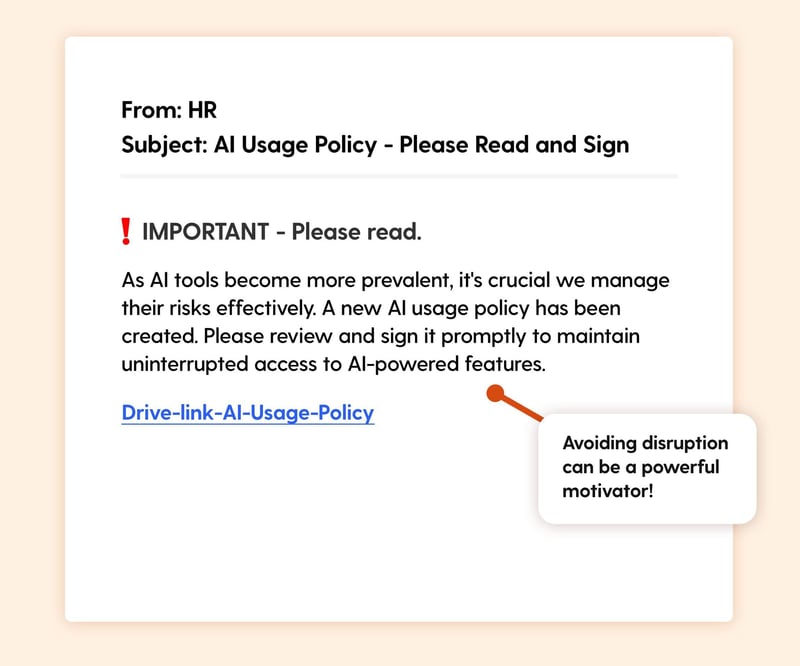
Scenario: Employees receive an email from “HR” informing them of a new AI policy that requires immediate acknowledgment. If they do not sign promptly, they risk losing access to AI-powered features at work.
The Hook: Emails from HR and IT departments tend to have high engagement rates because employees assume they are work-related and important. The mention of potential disruptions to workplace tools adds urgency, making it more likely that users will click.
Real-world risk: Clicking the link may lead to a fake HR portal, designed to capture login credentials or install malware.
Tips for spotting this phish:
- Be cautious of emails pressuring immediate compliance—legitimate policy changes come with notices and reminders.
- Look for sender address mismatches or formatting errors, which indicate phishing attempts.
Stay Alert in 2025
Cyber threats evolve rapidly, but with regular training and phishing simulations, organizations can stay ahead. These five phishing scenarios are a great way to keep employees engaged and prepared.
Want more phishing simulations? Browse our blog for additional templates and cybersecurity insights.
Ready to level up your organization’s cybersecurity? Register for a free trial of Wizer Boost and explore our full library of phishing templates and training exercises!
- Interactive Phishing Response Game
- Short, Randomized Challenges
- Encourage Proactive Responses
- Go Beyond A Typical Simulation
.png)

James Linton, Guest Writer
As a former email prankster turned social engineering and phishing expert, I'm passionate about helping individuals and businesses stay safer in their inboxes. By sharing practical insights on the ingredients of message based deception, and real-world examples of social engineering and phishing attacks, I aim to give fresh perspectives on how to understand the true nature of these problems.