Involved In A Data Breach?! What To Do Next
You've been notified that your account was involved in a company data breach - where does that leave you? First, you're not alone. With mega corporations the likes of Meta (aka Facebook), Amazon, T-Mobile, Discord, Pizza Hut/KFC, ChatGPT, Reddit, Atlassian, ad nauseum... all experiencing data breaches in the not-so-distant-past you bascially have to be living under a rock to not have had at least one account leaked to the dark web. Does this mean we just throw up our hands and do nothing accepting the inevitable? NO!
There are still actions within our control to protect our data and minimize harm, even in the event of a data breach.
This quick guide will walk you through the steps to take to ensure you've gone through all the basics after being involved in a data breach. As we mentioned in our previous guides on what to do if you're hacked on social media and what to do if your email is hacked, acting quickly to minimize unwanted access to your accounts is critical. Note you may download this guide below as a PDF to share with friends and family who may need it.
1 - Change Account Password immediately
When you find yourself caught in a data breach debacle, your first course of action should be to update your affected account password, making sure to strengthen and individualize it. Think of it as changing the locks on your door after discovering that an unauthorized person managed to get a duplicate key.
Now, while using the same password across many accounts for easy access is undeniably convenient, it's crucial to know that this habit also presents a well-known vulnerability. Cyber criminals thrive on this predictable behavior and use it against you to easily gain access to other accounts that reuse the same password.
What makes a strong password? Long + unique = strong
What's long? This changes as technology advances. A while back it was 6 characters, then 8. Fast forward to today and 'long' is defined as 12 characters or more for your password.
What's unique? To qualify as unique a password should meet the following criteria:
- Uses a mix of letters, numbers, and special characters (symbols such as !@_-.$)
- Does NOT include personal info like birthdays, street addresses, etc
- Does NOT include only a well-known song lyric or popular movie quotes
- Is NOT a password used by any other accounts or shared with another user
This can sound a bit of a tall order, however, using something called a passphrase is an easy way to create something unique without being a meaningless jumble of random numbers, symbols, and letters. See the image below for a quick guide on how to create a passphrase.
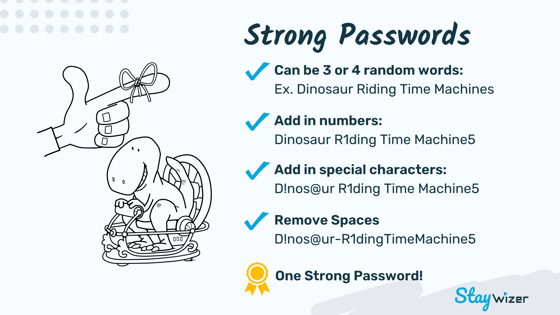
Also, consider a password manager to help you manage and use unique passwords across accounts without having to remember them all.
2 - Turn ON MFA/2FA
You've changed the digital lock to your account, now it's time to add a new deadbolt to it by turning on MFA/2FA, if you don't already have it on. Multi-factor or 2-factor authentication requires any new devices to verify the person logging in is really you and not just someone who happens to have gotten your password (like in the data breach you were sadly involved in through no fault of your own).
For most individuals, this additional form of verification means using an authenticator app like Google or Microsoft Authenticator or Authy. For accounts requiring a higher level of security, you may want to consider a Ubikey. Learn more about MFA and get quick links on where to turn it on for 16 of the most common apps here.
For most accounts, to turn on the MFA, look in the Settings either under 'Security' or 'Privacy'.
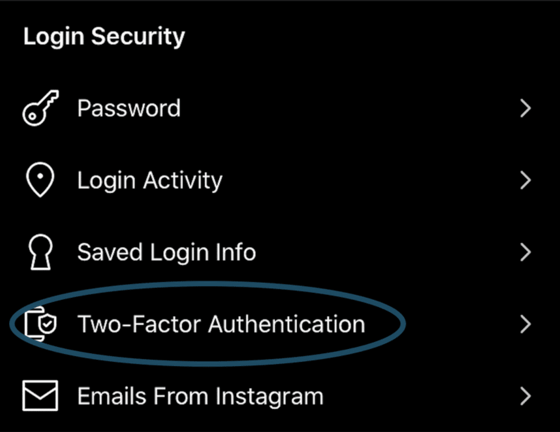
3 - Stop & Consider if Breached Password was Used for Other Apps. If so, rinse & repeat steps 1 & 2
As hinted at earlier, reused passwords are like giving cybercriminals a master key to any other accounts that share that password. If you still do it, you're not alone but you don't have to continue making it easy for the criminals. Take a moment to consider if there are any other accounts that use that same password that was involved in the data breach and then go to those accounts and update those account passwords to each be long and unique for stronger account protection.
4 - Critical Note! New Passwords Cannot Be ones in use by other accounts!
It may seem a bit much to emphasize this, but it's one of the most common ways criminals gain access so we just want to say it one last time (promise!) that any new passwords created for your breached accounts are passwords that have not been used for any other accounts.
Given that the typical internet user has 100+ digital accounts, this can seem overwhelming but that is where a password manager can greatly reduce frustration and increase security. Password managers can also generate long and unique passwords automatically when you need them and even monitor your accounts for being involved in data leaks.
5 - Set Up Transaction Alerts for Financial Accounts
If the account involved in the data breach was of a financial nature such as a banking app or an investing app, turn on notifications to be alerted to any transactions taken inside your account. This step is a good idea to do in any case as it will help you be aware of suspicious activity faster so you can take action as soon as you spot it.
6 - Contact the Breached Company For More Steps
You may have been alerted about the data breach from the company itself and they may have already sent a list of steps you can take to further secure your information, if so be sure and go through them. But not all breached companies communicate in a timely manner, or you may have discovered the breach through a data monitoring service such as through your password manager or through a site like haveibeenpwned.com. In that case, go ahead and reach out directly via the company's official contact page to request further information on what they recommend you do to further secure your data.
7 - Stay On Alert & Expect Increased Phishing Attempts!
With your account information now 'out there' thanks to the data breach, you can expect an increase in phishing emails and other scams targeting you. Just like companies sometimes sell your data to third parties for marketing purposes, so, too, the criminal marketplace takes breached information and resells it to their underground network. It's important that you know the basics of identifying a phishing email and educate yourself on some of the common scams by cybercriminals so that you can better protect yourself from these sneaky phishing attempts.
8 - Freeze Your Credit
Putting a freeze on your credit is a free and relatively simple process that provides an upgrade to protecting yourself against identity theft. Like setting up transaction alerts, this is not something you have to wait for a breach to do - you can get ahead of the game before a breach happens. You do need to submit the request to freeze your credit separately with each credit bureau but it's time well invested considering the security your giving yourself. While you're at it, consider freezing your child's credit, too, with our guide that walks you through the steps.
As mentioned in our other guides in this series "Hacked?! Now What?", online safety is about staying educated on current scams and creating good habits when you act online. If you're not sure where to start, check out our free guides below (no account needed) and follow us on social media on LinkedIn, Facebook, YouTube.
Wizer's Citizen's Online Safety Portal
Wizer's Family Online Safety Tips
Social Media Hacked?! Now What Do I Do?
Email Hacked?! What To Do Next
- Free Security Awareness Videos
- Quizzes
- Progress Reports and Certificates

Ayelet HaShachar Penrod
A passionate security awareness advocate, I connect and support security professionals as a Community Manager while also managing customer accounts for **Wizer Managed**, our security awareness service. Driven by 4 years of learning from cybersecurity experts, I’m committed to making security awareness accessible to all—individuals, small businesses, nonprofits, and enterprises alike.


