What is Phishing? And How to Avoid Phishing Scams
The internet is like a minefield of Phishing scams, and they are everywhere - Emails, Text Messages, Social Media, Ads, and even Google Maps. With DeepFake, Voice Cloning, and AI, some are so sneaky that they can fool even the most tech-savvy. This guide will explore phishing in-depth and show you how to spot them.
What is Phishing?
Phishing simply means an instance when scammers attempt to fool you into thinking they are someone else in order to make you do something. For example, they can steal your bank password by tricking you to click on a link and log into a fake website that looks exactly like your bank.
There are many types of phishing. Phishing emails are most common, but phishing is everywhere, phone, text messages, and social media. Scammers can purchase ads, register to dating sites, and even use celebrity look alike accounts.
Why Are Phishing Attacks So Effective
Even the most tech savvy people can get phished. Scammers operate like marketers and prey on people's emotions. It’s curiosity, fear, anger, greed, bias, and trust that make us vulnerable.
Scammers use scare tactics to cause anxiety. This often shuts off people's filters and ability to make good judgments.
Here is an example of a spear phishing email: Imagine I hacked your mother’s account and sent you a phishing email message that read - “I got my test results from the lab but I can’t open them, I asked Jenny, and she also couldn’t. Can you help me?” What would you do? The email looks legit, it’s from your Mom’s email address. Who wouldn’t want to help their own mother, right?
There are many reasons why people fall for these phishing scams - If someone has money issues, is sick, or lonely (very common since COVID-19), then a “solution” comes along they may just want to believe it’s true.
And then there is also “change blindness”, Watch the video below:
Did you SEE that! Would YOU have spotted the change? Half of the people didn’t. The reason is that when we focus on one thing, like giving directions we are somewhat blind to other things. Which is also the reason why people fall for online scams.
When we replay the incident after the fact, it seems obvious and we can’t believe we fell for it. HOWEVER, we were not given a heads up when it happened. Our brain is unable to properly see situations for which we have no prior experience.
These days we live in a world where we are constantly moving and everything seems to have a sense of urgency. We are in a hurry, on mobile devices most of the time, and sometimes we click on things accidentally! And scammers use that against us.
11 Types of Phishing Scams You Should Know About
1. Email Phishing Scams
This is probably the most common phishing scam out there, but still very effective. It may look like an email from your bank, Paypal, Google, Amazon, or even your CEO. Some phishing emails are generic, meaning the scammers didn't target you specifically. They just email blasted thousands or millions of contacts. They know that statistically some people will fall for the scam.
Then there is spear phishing, where they target you specifically. They did their homework. They have researched you, they know your family members, where you work, and who is your boss. They have invested time in getting to you and the chances of fooling you are higher.
Here is a spear phishing example of how a company was scammed out of $1 million dollars and it all started with a single spear-phishing email.
2. Smishing Scams
These are text message phishing scams. This has become a criminal's favorite. They know people respond to text and instant messages faster than email. And phone numbers are easy to obtain. Just as with email, some smishing attacks are generic, meaning they didn't target you specifically, while others are targeted similar to email spear phishing.
Watch this live smishing attack
Here are 5 more eye-opening smishing attacks that will freak you out.
- How they bypassed Mike's multi-factor authentication in seconds.
- How they hacked an entire 9th grade with this nasty text scam.
- How deep fake was used in this dating scam.
- How Donna's Office365 account was hacked.
3. Google Search Scams
You may be surprised, but some of the top search results in Google are phishing links. Scammers also invest in search engine optimization and work hard to rank their scam sites in the top search results.
4. Scam Ads
You see an Ad on Facebook and you assume it’s legit, however Facebook is full of Scam Ads and is a scammers’ paradise! Unfortunately, many people blindly trust Ads that appear on "reputable” sites and assume these sites filter out scams. And it’s happening everywhere…not just Facebook. We created this quick guide to show how to spot Fake Ads.
5 TIPS to spot scams Ads:
👉 Google the product or the website name along with the phrase "scam."
👉 Google the exact wording in the ad. Many scams can be found this way.
👉 If you are constantly served the same ad and the price is dropping, it's probably a scam.
👉 If most of the reviews are within several days, then they are probably fake.
👉 If they ask you to pay using PayPal Friends and Family - You won't get your money back.
5. Social Media Phishing Attacks
“One fake friend can do more damage than five enemies” Social media is full of fake accounts. These fake accounts are even used by nation states to infiltrate a community, collect intel about what’s going on, or to influence it. It could also be a fake account with the same name and photo as one of your real friends that will later try to scam you.
This is a real-life story about how she was phished on LinkedIn
Here's 6 more examples for HOW you can get phished on social media.
You get a message from:
👉 A friend whose account was hacked and is now sending you a PDF/Link as a followup to a chat you started a while ago.
👉 You respond to a fake job offer.
👉 You are willing to help someone with a research paper. You download the pdf and boom...
👉 A fake investor wants to invest in your business.
👉You download an app suggested by a well known content creator that you follow. The content creator was paid by a scammer without realizing it’s a scam.
👉 You are offered an advisory board position by a fake company or a hacked account.
6. Fake Business Listing on Google Maps
Unfortunately, millions of business listings on Google Maps are scams. Scammers can hijack the name of a legitimate business on Google Maps and list their own fake phone number and fake website. If you click on the link or call, it will be the scammer that answers.
7. Fake Job Postings
Unfortunately, scammers are posting fake jobs on major job sites or impersonating companies that have job posts. Job scams are one of the worst! When you send a W-4 to a fake employer (scammer) it includes all your personal information, this info is enough to steal your identity, create a fake social security card, collect your tax returns, and even vote on your behalf. They may even ask for financial information right up front, or will go the easy route and just email you with some fake link or malicious attachment!
8. QR Codes Scams
Who thought a QR code can be dangerous? They are everywhere, especially in restaurants. Criminals can place their own sticker over the legitimate one. So that when you scan it, you will be redirected to a fake site.
9. Vishing Attack
Vishing (voice phishing) is a type of phishing attack made over the telephone. Unfortunately, this happens too often. Scammers can spoof a phone number that looks identical to a known number, like your bank. In this true story, she lost it all, the inheritance that was supposed to be the future for her children, and peace of mind. All Gone in 5 minutes.
Scammers also register phone numbers that are almost identical to those of known brands. They target those who miss-dial. They answer and pretend to be the company you think you were calling.
How they hacked her bank account over the phone
10. Dating and Romance Scams
Dating scams are VERY common! After all, you are ready to meet a new stranger... This is like a haven for scammers. This can turn to a romance scam, where you fall in love with a scammer and they get you to pay for things. Or a blackmail scam, where they get you to send a nude photo and blackmail you. Or just get you to click on a phishing link
11. Fake Apps and the App Store
Unfortunately, we can't blindly trust the App Store. There are millions of apps in the App Store and scammers found ways to list their own apps. Some will steal your information and others your money. The following Wizer story is based on a TRUE story we dramatized (it’s played by an actor).
She HAD about 5 bitcoins and minutes later it was all GONE!
Phishing Scam Trends for 2022
Deep Fake
We are at a point where technology is outpacing the ability of society and government to adapt. With DeepFake, Voice Cloning it’s becoming almost impossible to Identify what’s real and what’s not.
Imagine someone hacked your social media account and is now posting DEEP FAKE videos of you saying things you never said - trying to scam your followers.
They posted DeepFake Videos of him advising others to buy bitcoin
Or they pretend to be your grandson calling from jail and asking you to bail them out.
Supply Chain
Businesses rely heavily on other 3rd party suppliers. This could be hardware vendors, like computers or smart devices. Or software solutions, like the HR system or even Google Docs. So how do you know if the invoice you received from your supplier is legitimate or a phishing email scam?
Also, what if criminals hacked one of your suppliers? For example, if they hack the HR vendor you are using and added some malicious code or just stole your data. Now they will be able to hack all their customers.
The reason this is becoming common is because vendors are pushing their teams to develop new features and often there isn’t time left for security. It ultimately becomes someone else’s problem when it is too late.
Software Developers
If a criminal can hack a developer, they can add a backdoor into the solution the developer is working on. Developers use libraries, which are basically other people’s code packaged nicely. It takes one line of code to include a library that someone else developed in your app. But what if the developer had a typo and downloaded a look-alike library that is identical to a legit library, with the addition of malware or a backdoor.
Live Demo - Hacking Copy and Paste!
The developer may not even realize this because everything works, and you don’t realize it because the app you downloaded works just fine. But the criminals happily realize it because now they have full access to your computer.
Spear Phishing vs. Phishing: What’s the Difference?
Unlike standard phishing email attacks, which are more generic, a spear phishing email is a more personalized email attack. The amount of information a criminal can obtain about anyone simply by using an online background check is alarming. With this information, they can craft a personalized phishing email that looks amazingly authentic.
Here is an example of a spear phishing email attack: Let's say you are a sales guy. A criminal can figure out where you work because they found you on LinkedIn. They may also know who your customers are, because they read your customer testimonials. Using this info they email you a fake purchase order at the end of the quarter, that looks like it's from one of your customers. Will you open it? If yes, it will infect your computer with malware. Nasty, right? That’s a spear phishing attack. The more they know about you, the easier it is to fool you.
What Helps Protect You From Phishing Attacks
We often say “Think Before You Click” - and It’s great advice! However, people still click before they think. Why? It’s because it isn’t just about knowledge. We all learned about stop signs and when to hit the brakes, however there are still a ton of accidents out there.
We are emotional creatures, we feel before we think, we are curious, biased, and sometimes overly optimistic. That’s why routines and HABITs are so important. They act like guardrails.
Even starting with adopting only one habit will significantly increase your awareness, and slowly, you will add more.
Before responding or clicking on a link, make the following habits:
- If it’s urgent, don’t let the emotions cloud your judgment - If you get an urgent email from your boss, a text message from your bank, or see an amazing deal on Facebook, take a moment, let the emotions settle down, and read it out loud. Does it make sense, could it be a phishing email? The clock is also ticking for scammers, they need you to act fast before you realize you are being scammed. So don’t let them!
- Call and Verify! - One of the best ways to fight against a phishing attack is to verify that you are talking to the correct person. For example, when you are purchasing a house, someone can spoof your attorney’s email and send you fake wiring information. So, call and verify.
- Check the Address - Always check the email address and URL for spelling mistakes. Whenever you need to login, it’s better to manually type in the URL instead of clicking on the link in the email. Even though checking for any spelling mistakes in the sender address is a MUST, that by itself is not enough, because there are ways to spoof an email address to make it look identical to the real one. So whenever you need to take action, like sending sensitive information, transferring money, or logging in, make it a habit to call the sender and verify.
- Enable Multi-Factor Authentication - Let’s say you got fooled by an email phishing scam and they hacked your gmail account, now they can start hitting “reset password” on your other apps, and guess where the reset password link ends up at? Your hacked gmail account. And that’s why a password isn’t enough to secure your digital life. We need a second authentication method or what is usually referred to as Multi-Factor Authentication. It’s when you need to type in a code after you enter your password to finish logging in. This code is either sent to your phone or generated by an app that creates new codes usually every 45 seconds. This way, even if your password was stolen, they don’t have that second code to get in. Many apps have this option, but it’s turned off by default, you can usually find it in settings -> privacy or security and look for Multi or Two Factor Authentication. Using an Authenticator App is the preferred method, because scammers found ways to also fool you to give them the code that was sent to your phone. Microsoft or Google Authenticators are two apps that you can download from the app store that will generate these codes for you. We have create a great guide about How Multi Factor Authentication Can Save You with an MFA Cheat Sheet for 15 common apps and much more.
- Look at the Style of the Message - like, does the style of the email feel different from previous emails you received from that particular person. Are you expecting this email? Does it cause you angst, stress, euphoria, happiness, or any other emotion that makes you want to do something?
- Ask Questions - If the suspicious message is from a family or a friend, you can ask simple questions that only you and they know. If it’s your CEO or someone you don’t directly report to and you feel uncomfortable calling them, talk to your manager.
- Security Awareness Training - Education and acquiring cyber safety habits is KEY. The more you know about scams, the better you spot them. A good security awareness training will include relatable real-life stories and tips that can help us protect our digital lives wherever we are - at Work or Home.
3 Examples of Real Life Phishing Email Attacks?
1. Employee New Time Off Policies
Who doesn't care about Time-Off? The curiosity and sense of urgency makes this phishing email very effective.

2. You Got Hacked
This is a typical phishing email. Someone is trying to hack you and you need to take action immediately to prevent them from taking over your account. Once again the sense of fear and urgency is used to cloud our judgment.
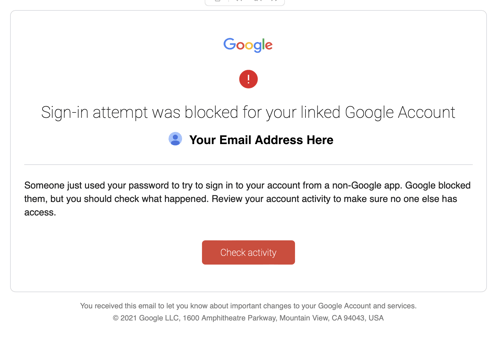
3. The CEO wants to meet
Why does the CEO wants to meet me? This is a spear phishing attack. They know the CEO's name and even the links looks legit, however when you hover over it you will find it's a phishing scam.
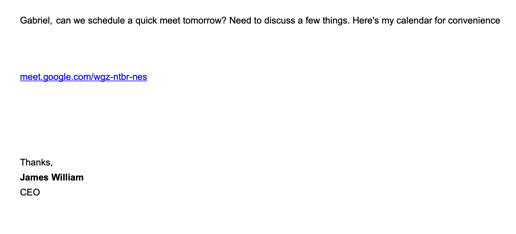
What is Phishing Training for Employees
Training employees to spot phishing attacks is a MUST in fighting phishing attacks. It’s a core component of any good security awareness training. Your team can be a human firewall if they are trained well. And it’s not just about not clicking on phishing links, It's also about reporting. The sooner you know about a phishing attack, the sooner you can warn others in your team. There are several components to phishing training for employees.
Education - This could be online videos that employees must watch and then take quizzes, in-class sessions, or both. It is also crucial to include training in new employees’ onboarding process. New employees are an easy target because they don’t know many of their co-workers, and criminals may easily fool them. Security awareness doesn’t come naturally, and changing habits takes time. So education must be an ongoing effort throughout the year and not a one-time event.
Here is how Wizer's Security Awareness Training Looks Like
Training - After your team learns about phishing, it’s time to practice what they learned. This can be done through gamification and other exercises to help identify phishing emails vs. legitimate emails.
Simulation - Phishing Simulation means that you will be phishing your team to test the effectiveness of your phishing training. Those who fail the phishing test will get an explanation of what they can do next time to spot these phishing emails better.
What is a Phishing Simulation?
It's an effective way to determine how likely your employees will click on real phishing emails, by simulating a phishing attack. However don’t expect a zero click rate, because it isn’t realistic, it basically means no one is vulnerable.
Here is what Wizer's Smart Phishing Simulation Looks Like
How To Report Phishing
- Wizer Phish Alert Button Allows end-users forward potential phishing emails to your internal security team for analysis.
- Report it to the Anti-Phishing Working Group (APWG) by forwarding the phishing email to reportphishing@apwg.org.
- Report it to Google - you can report the URL and submit it to Google SafeBrowsing.
- Report it to the Federal Trade Commission, here you can report any scams.
Ready to launch your next phishing campaign? Register now for a free 10-day trial of Wizer Boost to explore all of Wizer’s Phishing Simulation Templates and Phishing Exercises.

Gabriel Friedlander
Gabriel Friedlander is the Founder & CEO of Wizer, whose mission is to make basic security awareness a basic life skill for everyone. Wizer has been rapidly growing since being founded in 2019, and now serves 20K+ organizations across 50 countries. Before founding Wizer, Gabriel was the co-founder of ObserveIT (acquired by Proofpoint). With over a decade of experience studying human behavior, he is a prolific content creator on social media, focusing on online safety to elevate public understanding of digital risks. His engaging 1-minute videos have captured the attention of millions worldwide, going viral for their impactful messages.


